Flag on the Play!

Clutch Top Company - Local SEO Company 2024

Certified Digital Marketing Strategist
Clutch Top Women Owned Web Design Company - 2024
Expertise.com Best Web Designers in Raleigh 2024 Badge

Top Digital Marketing Company - Clutch - North Carolina 2024

Google Partner Premier 2023
Over the past week or so, there have been numerous attacks on WordPress sites. These “low-baller hackers” are looking for unattended sites to distribute links to porn sites & canadian pharmacies, as well as install malware on users computers.
How Do I Check My Site?
Most of the time, you can’t see the initial changes just by looking at your site or logging in. If you’ve had an initial attack, the script may be “hidden” in your page HTML but redirecting some unsuspecting visitors. Once your site gets logged as an “open” site, other hackers join the party and have a happy time adding their own mess to your site. At some point, you may start to see “Click here to buy cheap viagra” links replace random images or navigation items. If you can SEE the problem visibly on the public side of your site, odds are there are much bigger problems. Here’s a step by step process to check your site:
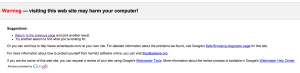
- Google your company name or site. Make sure the listing in search results looks normal. A site flagged by Google will have a snippet like this under your site title:
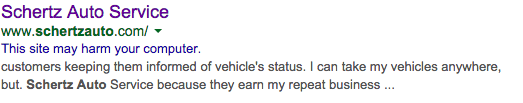
- Go to your site thru the search engine link. If you don’t end up on your home page, and are redirected elsewhere, you have a problem.
- Check the links on your header, navigation, sidebar and footer. The header & footer of a page are most often targeted.
- Login to your Google Webmaster Tools. Messages regarding malware will be in your inbox for this account. DON’T IGNORE THEM.
- If you are familiar with HTML, you can view the source of your web page in your browser. Look at the blue underlined sections of code, since these are links to outside sites. Check for links you do not recognize.
If you see the screenshots below while trying to access your website, you’ve not only been infected, but Google has started warning your site visitors to stay away:
[van_one_half_last]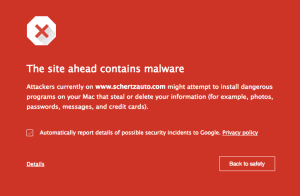 [/van_one_half_last]
[/van_one_half_last]
I’m Infected!! Now What?
If you find something unfamiliar, see the message from Google in your search results or Webmaster Tools, or are redirected outside of your site, action needs to be taken immediately.
Cleaning Your Files Yourself
Depending on how web-savvy you are, you can look through your site directory in your host for unfamiliar files, and last edited dates. If you have WordPress, an easy way to get rid of extra/infected files is to purge the files (except wp-config & htaccess) in your main directory, as well as the wp-admin & wp-includes directories. Download a fresh copy of WordPress and replace them with these files. If you use this method, it is important that you DO NOT DELETE your wp-contents directory, since this contains your theme, photos, and plugins. Those directories will need to be manually cleaned unless you have a clean copy to replace them with. Some hosts will provide a complimentary scan of your site once you have cleaned/replaced your files to make sure the problem is gone.
Having Your Host Help
Some web hosting companies will provide a cleaning/updating service at no charge. Some will only quarantine infected files (in this case, take what you can get, at least they’re helping you find the problem). Some hosts (usually the less expensive accounts) will not help with the process at all. The easiest way to find out is just to call and ask.
Contacting a Provider to Help You
If you are not sure how to go about cleaning your site, and your host will not assist, contact a professional. Contrary to what some may say, YOU DO NOT NEED TO ABANDON YOUR DOMAIN NAME. If you are in the worst possible position, you can still clean your site and request a reconsideration through Google. While this process still takes up to a week or so, it is still quicker than starting over, especially if your site has a good reputation and does well with ranking. Here is what you should be asking for:
- Review of the site’s files & directories. Once a suspicious file has been located, note the date it was last edited.
- Review and clean/deleting files that have suspicious scipts and links. Note additional files with the same edit date, check to see if they are required by your site or were uploaded by the hacker.
- Change ALL your passwords. Consider changing usernames, especially if you use “admin”.
- Remove unnecessary users from your site, host & database.
- Update your software and plugins.
- Consider installing additional security. A good one for WordPress is WP All In One Security.
I Didn’t See A Problem, But How Can I Prevent It From Happening?
If you are sure you are in the all clear, consider:
- Updating your usernames and passwords as a preventative measure.
- If you use WordPress or another content management system, install additional security. A good one for WordPress is WP All In One Security.
- Remove unnecessary users from your site, host & database.
- Make sure you login to your site regularly and keep your software and plugins up to date.
The Worst Thing You Can Do
The absolute, most terrifyingly worst ever thing you can do is…ignore a potential problem. If you are in the service business and don’t know if your site is functioning properly, all your potential customers could be sent away from your site due to an infection. Your pay-per-click ads will no longer function, your site will disappear from search results, and the few visitors you get will be repeatedly warned not to enter your site. The potential for lost income is huge, so don’t ignore it! Check your site!